· Alex · security · 16 min read
Microservices Security
Architecture, security challenges, monitoring, logging and best practices for microservice security
Microservices Security
What exactly are microservices?
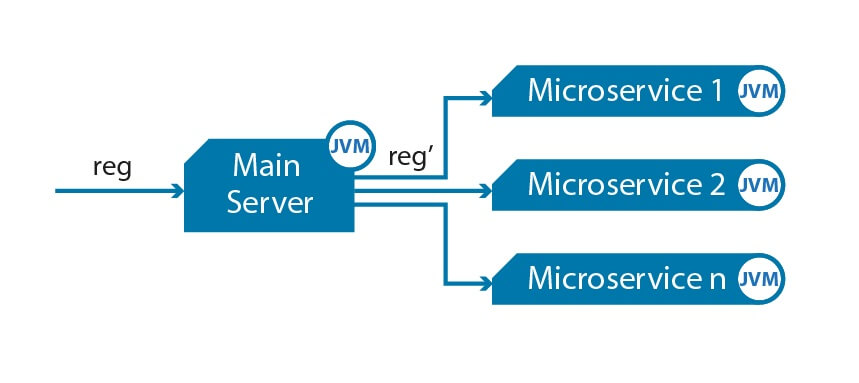
Microservices architecture is a modern approach to developing software applications by breaking them down into smaller, independent, and modular components. These bite-sized building blocks, known as microservices, are designed to work together to create a full-fledged application. Each microservice is responsible for a specific functionality, and they communicate with each other via APIs (Application Programming Interfaces). The goal of this approach is to enhance scalability, maintainability, and flexibility, which allows developers to make updates or troubleshoot issues without taking the entire system down.
Although microservices come with a slew of benefits, they also introduce new security challenges that can’t be ignored. The complex nature of microservices, the increased number of APIs and endpoints, and the need for secure communication between services are just a few examples of these challenges.
Understanding Microservices Architecture
Definition and key concepts of microservices
These independent building blocks, aka microservices, communicate with each other through APIs to create a complete application. The core concepts of microservices include modularity, scalability, and decoupling, which make it easier to develop, maintain, and update applications.
Benefits of microservices architecture
- Scalability: Since each microservice can be scaled independently, it’s much easier to manage the application’s growth and allocate resources efficiently.
- Flexibility: Independent services allow for quicker and more flexible updates, as developers can modify or add new features without affecting the entire application.
- Maintainability: Microservices simplify the debugging and maintenance process, as issues can be isolated and resolved without impacting other parts of the system.
- Technology stack diversity: Each microservice can use its own technology stack, offering the freedom to choose the most suitable tools and languages for specific tasks.
Common use cases
Microservices architecture is an excellent fit for various scenarios, such as:
- Large-scale applications with rapidly evolving business requirements.
- Applications that demand high availability and reliability.
- Applications that require a diverse technology stack for different components.
Comparing microservices with monolithic architecture
Key differences
Microservices and monolithic architectures differ in several ways:
- Structure: While microservices break an application into small, independent components, monolithic architecture builds it as a single, cohesive unit.
- Scalability: Microservices can be scaled individually, whereas monolithic applications require scaling the entire system.
- Deployment: In microservices, each component can be deployed independently, while in monolithic applications, any change requires redeploying the entire application.
Pros and cons of both architectures
Microservices:
- Pros: Better scalability, maintainability, flexibility, and technology diversity.
- Cons: Increased complexity, potential security challenges, and a need for well-defined communication and coordination between services.
Monolithic:
- Pros: Simpler architecture, easier to build and deploy, and a unified codebase for the entire application.
- Cons: Limited scalability, increased difficulty in updating or maintaining the application, and a single technology stack.
Common Microservices Security Challenges
Increased attack surface
The increased attack surface is one of the major security concerns when dealing with microservices. The more distributed your architecture becomes, the more potential entry points there are for attackers. This complexity can make it harder to keep track of all the components and their interactions, leading to possible security gaps.
Complexity of microservices
The very nature of microservices – being small, independent, and distributed – can be a double-edged sword. While it offers advantages like scalability and maintainability, it also adds complexity to your application. This complexity can manifest in several ways:
- Communication: As the number of microservices grows, so does the need for them to communicate with each other. This can lead to a tangled web of interactions, making it difficult to identify potential security weaknesses.
- Service discovery: In a distributed environment, services need to locate each other to exchange information. Managing and securing this process can be challenging.
- Configuration management: Each microservice may have its own configuration settings, increasing the risk of misconfigurations that can expose vulnerabilities.
Increased number of APIs and endpoints
APIs play a critical role in microservices architecture, as they enable communication between services. However, the more microservices you have, the more APIs and endpoints you need to manage. This can lead to a range of security challenges:
- API vulnerabilities: Insecure APIs can provide an easy entry point for attackers. Ensuring the security of each API becomes crucial to protect your application.
- Rate limiting: Without proper rate limiting in place, attackers can flood your APIs with requests, potentially leading to a denial-of-service (DoS) attack.
- Versioning: As your microservices evolve, so will your APIs. Managing multiple API versions securely can be a daunting task.
Authentication and authorization
In a microservices architecture, it’s essential to have a robust authentication and authorization system in place. With multiple services interacting with each other and possibly external systems, you need to make sure that only authorized users and services can access sensitive information or perform specific actions.
Consistent access control across services
Here are some tips to help you achieve this:
- Centralized identity management: Use a centralized identity management solution, such as OAuth 2.0 or OpenID Connect, to manage user authentication and authorization across all your microservices. This approach simplifies access control management and promotes consistency.
- Role-based access control (RBAC): Implement RBAC to define different levels of access and permissions for users and services. This enables you to enforce fine-grained access control policies consistently across all microservices. See my post on REST API authorization best practices
- Service-to-service authentication: In addition to user authentication, it’s vital to authenticate the communication between services. Use techniques like mutual TLS (mTLS) or API keys to verify the identity of services before allowing them to interact.
Secure token management
Token management is a critical aspect of authentication and authorization in microservices, as tokens are often used to represent a user’s or service’s identity and permissions. To keep your system secure, follow these best practices for token management:
- Use short-lived tokens: Short-lived tokens minimize the risk of unauthorized access in case a token gets compromised. Refresh tokens can be used to obtain new access tokens without requiring users to re-authenticate.
- Token storage: Store tokens securely, either in encrypted cookies or secure client-side storage like the Web Storage API. Avoid storing tokens in URLs or local storage, as they are more vulnerable to attacks.
- Token validation: Always validate tokens on the server-side to ensure they haven’t been tampered with. For JWT (JSON Web Token) tokens, make sure to verify the signature and check the token’s expiration time.
- Token revocation: Implement a token revocation mechanism to invalidate tokens when necessary, such as when a user logs out or their permissions change. This can help prevent unauthorized access in case a token is compromised.
Monitoring and logging challenges
Monitoring and logging are crucial components of any secure application, and they become even more critical in a microservices architecture. Due to the distributed nature of microservices, keeping track of logs and monitoring data from multiple services can be a daunting task. Let’s explore some strategies to overcome these challenges.
Centralized logging for distributed services
In a microservices environment, logs are generated by numerous independent services, making it difficult to correlate events and identify potential security threats. Centralized logging can help alleviate this issue by consolidating logs from all services into a single, unified location. Here are some tips for implementing centralized logging:
- Use log aggregation tools: Leverage log aggregation tools like Logstash, Fluentd, or Graylog to collect, process, and store logs from all your microservices in a centralized location.
- Standardize log formats: Ensure that all your services use a standardized log format, making it easier to parse, analyze, and correlate log data.
- Implement log retention policies: Define and enforce log retention policies to determine how long logs should be stored, taking into consideration both storage limitations and compliance requirements.
- Secure log data: Secure your log data by encrypting it both at rest and in transit, and by controlling access to the centralized logging system.
Anomaly detection and response
Detecting and responding to anomalies is crucial for identifying potential security threats and mitigating their impact. With a centralized logging system in place, you can more effectively monitor your microservices and detect unusual patterns or behaviors. Here’s how to enhance your anomaly detection and response capabilities:
- Implement monitoring tools: Use monitoring tools like Prometheus, Grafana, or Datadog to collect and visualize metrics from your microservices, making it easier to spot anomalies.
- Set up alerts: Configure alerting mechanisms to notify you of any unusual activity or potential security threats detected in your logs or metrics.
- Perform log analysis: Regularly analyze your logs to identify trends, patterns, or anomalies that may indicate security issues or vulnerabilities. Consider using machine learning or artificial intelligence-based tools to help automate this process.
- Establish incident response procedures: Develop and implement incident response procedures to handle potential security threats quickly and effectively. This includes defining roles and responsibilities, communication channels, and steps for containment, eradication, and recovery.
Best Practices for Microservices Security
Secure development lifecycle
Incorporating security into every phase of the development lifecycle is crucial for building and maintaining secure microservices. A secure development lifecycle helps ensure that security considerations are not an afterthought but an integral part of the entire process.
Security by design
Security by design means making security a priority right from the start, and integrating it into every stage of your development process. Here are some ways to achieve security by design:
- Establish security requirements: Define clear and specific security requirements for your microservices, taking into consideration factors like data sensitivity, compliance, and potential threats.
- Incorporate security into the development process: Make security an integral part of your development process by following secure coding practices, using security-focused tools, and regularly reviewing and updating your code to address potential vulnerabilities.
- Encourage a security mindset: Foster a culture of security awareness among your development team, providing ongoing training and resources to help them stay up-to-date with the latest threats and best practices.
- Automate security checks: Use automated tools to perform static and dynamic code analysis, dependency scanning, and other security checks as part of your development pipeline.
Threat modeling and risk assessment
Threat modeling and risk assessment are essential activities for understanding potential risks and vulnerabilities in your microservices. By proactively identifying and addressing threats, you can minimize the likelihood of security incidents and reduce their potential impact. Here’s how to get started with threat modeling and risk assessment:
- Identify assets: Determine the critical components and data in your microservices that need to be protected, such as sensitive information, APIs, and communication channels.
- Define threat scenarios: Identify potential threat scenarios that could impact your microservices, taking into consideration factors like possible attack vectors, attacker capabilities, and the likelihood of exploitation.
- Evaluate risks: Assess the potential impact of each threat scenario on your microservices and prioritize them based on factors like severity, likelihood, and potential damage.
- Implement countermeasures: Develop and implement countermeasures to mitigate identified risks, such as implementing strong authentication and authorization mechanisms, encrypting data at rest and in transit, and using network segmentation.
Authentication and authorization
A robust authentication and authorization system is a must-have for any secure microservices architecture.
Implementing OAuth 2.0 and OpenID Connect
OAuth 2.0 and OpenID Connect are widely-used standards for authentication and authorization, and they can help you manage user identities across your microservices effectively. Here’s how to implement them:
- Use OAuth 2.0 for authorization: OAuth 2.0 is an industry-standard protocol for authorization. It enables you to grant third-party services limited access to your microservices on behalf of users, without sharing their credentials. Implementing OAuth 2.0 can help you manage access control in a secure and standardized way.
- Use OpenID Connect for authentication: OpenID Connect is an authentication layer built on top of OAuth 2.0. It allows you to authenticate users and obtain basic profile information in a standardized manner. By implementing OpenID Connect, you can simplify user authentication and ensure a consistent user experience across your microservices.
- Choose an identity provider (IdP): Select an IdP that supports OAuth 2.0 and OpenID Connect, such as Okta, Auth0, or Google Identity Platform. The IdP will manage user authentication, issue tokens, and handle token validation, reducing the complexity of implementing these standards in your microservices.
Role-based access control (RBAC)
RBAC is a powerful technique for managing access control in a granular and consistent manner. By implementing RBAC, you can define different levels of access and permissions for users and services based on their roles. Here’s how to implement RBAC in your microservices:
- Define roles and permissions: Start by identifying the various roles within your application, such as admin, user, or guest, and define the corresponding permissions for each role. This may include actions like read, write, delete, or execute.
- Assign roles to users and services: Assign the appropriate roles to users and services based on their responsibilities and access requirements. This may involve mapping roles to user groups or using attributes from the authentication process to determine role assignments.
- Enforce access control policies: Implement access control policies based on the assigned roles and permissions, ensuring that users and services can only perform actions they are authorized to. Use tools like API gateways, middleware, or policy enforcement points (PEPs) to enforce these policies consistently across your microservices.
Encryption and data protection
Protecting your data is a top priority when securing your microservices, and encryption plays a vital role in achieving this goal. By implementing strong encryption and key management practices, you can keep your sensitive data safe from prying eyes.
Data encryption at rest and in transit
Encrypting your data both at rest and in transit is essential for maintaining the confidentiality and integrity of your data. Here’s how to implement data encryption for your microservices:
- Data encryption at rest: Use encryption methods like Advanced Encryption Standard (AES) or Transparent Data Encryption (TDE) to protect data stored in databases, file systems, or other storage systems. Make sure to use strong encryption keys and algorithms, and consider using encryption tools provided by your storage system or third-party solutions.
- Data encryption in transit: Secure communication between your microservices by implementing Transport Layer Security (TLS) to encrypt data transmitted over the network. This will protect your data from eavesdropping, tampering, and other threats. Also, ensure that your microservices only accept connections from trusted sources and that they validate certificates to prevent man-in-the-middle attacks.
Key management best practices
Proper key management is crucial for maintaining the security of your encrypted data. By following these best practices, you can ensure that your encryption keys remain secure and confidential:
- Secure key storage: Store your encryption keys securely, using methods like hardware security modules (HSMs), key management services (KMS), or dedicated secrets management solutions. Avoid storing keys in plain text or in easily accessible locations. If you’re using Java, perhaps my post on a reasonably secure way store to store a secret in Java can help a little.
- Access control: Limit access to your encryption keys by implementing strong access control mechanisms. This may include role-based access control, multi-factor authentication, or other security measures.
- Key rotation: Regularly rotate your encryption keys to minimize the impact of potential key compromises. Develop a key rotation policy that defines the frequency and circumstances under which keys should be rotated, as well as procedures for handling key changes.
- Key backup and recovery: Maintain secure backups of your encryption keys to ensure that you can recover your data in the event of a key loss or system failure. Implement a robust key recovery process that includes safeguards to prevent unauthorized access.
API security
APIs are the backbone of microservices communication, and securing them is a top priority. By following these best practices, you can ensure the security and reliability of your APIs:
Proper API design and versioning
A well-designed and consistently versioned API is crucial for maintaining security and usability.
- Use RESTful principles: Adopt RESTful design principles for your APIs, which promote a standardized, stateless, and easily understandable interface. This can help reduce potential security risks and make your APIs more maintainable.
- Implement versioning: Use versioning for your APIs to ensure that updates and changes don’t break existing clients. This can help you maintain a secure and stable API, while still allowing for improvements and bug fixes. Consider adopting semantic versioning or using version numbers in your API’s URL or request headers.
API gateways and rate limiting
- Use API gateways: Implement an API gateway to act as a single entry point for your microservices. This can help you centralize authentication, authorization, and other security policies, making it easier to manage and monitor your APIs. Popular API gateways include Kong, Apigee, and AWS API Gateway.
- Implement rate limiting: Enforce rate limiting on your APIs to prevent abuse and protect your services from distributed denial-of-service (DDoS) attacks or excessive resource consumption. Rate limiting can be implemented at the API gateway level or within your microservices, using techniques like token bucket or leaky bucket algorithms.
- Monitor and log API traffic: Regularly monitor and log your API traffic to detect potential security issues, performance problems, or other anomalies. Use centralized logging and monitoring tools to gather and analyze API data, and set up alerts to notify you of any unusual activity.
Container security
Secure container orchestration
Container orchestration platforms, such as Kubernetes, Docker Swarm, or Amazon ECS, help manage and scale your microservices. Securing your container orchestration platform is crucial for maintaining the overall security of your microservices. Here’s how:
- Use strong authentication and authorization
- Enable network segmentation: Use network segmentation to isolate your microservices and minimize the potential impact of security incidents. This can be achieved using techniques like Kubernetes namespaces, network policies, or virtual private clouds (VPCs).
- Implement resource limits: Set resource limits on your containers to prevent them from consuming excessive system resources and causing performance issues or denial-of-service (DoS) attacks. This may include CPU, memory, or disk space limits.
- Keep your orchestrator up-to-date: Regularly update your container orchestration platform to ensure that you’re running the latest security patches and features. This can help protect your system from known vulnerabilities and improve its overall security posture.
Container scanning and vulnerability management
Regularly scanning your containers for vulnerabilities and managing potential risks is essential for maintaining a secure microservices environment.
- Scan container images: Use container scanning tools, such as Docker’s built-in scanning, Anchore, or Clair, to identify vulnerabilities in your container images. This should include scanning for outdated or insecure components, misconfigurations, or other potential risks.
- Integrate scanning into your CI/CD pipeline: Incorporate container scanning into your continuous integration and continuous deployment (CI/CD) pipeline to detect vulnerabilities early in the development process. This can help you address security issues before they make it into production.
- Patch and update containers: Regularly patch and update your containers to address known vulnerabilities and minimize the risk of exploitation. This may include updating base images, upgrading software components, or applying security patches.
- Implement vulnerability management processes: Develop a vulnerability management process that includes identifying, assessing, prioritizing, and remediating vulnerabilities in your containers. This should involve tracking vulnerabilities, assigning responsibility for remediation, and monitoring progress.
Conclusion
Throughout this blog post, we’ve seen how microservices architecture has revolutionized software development by enabling greater agility, scalability, and flexibility. However, this architectural shift also comes with its own unique security challenges, making microservices security a critical aspect of application security. As we’ve discussed, ensuring the security of microservices-based applications involves addressing issues such as authentication, authorization, data security, API security, container security, and monitoring and logging. By adopting the best practices outlined in this blog post, you can build a solid foundation for securing your microservices-based applications and protect your organization and users from potential security threats.
About the Author:
Application Security Engineer and Red-Teamer. Over 15 years of experience in Application Security, Software Engineering and Offensive Security. OSCE3 & OSCP Certified. CTF nerd.