· Alex · security · 7 min read
What Does AES Stand For?
How AES works and how it applies to application security
What Does AES Stand For
The Advanced Encryption Standard (AES) is a symmetric key encryption algorithm that has become the gold standard for securing digital data. AES was developed as a result of the National Institute of Standards and Technology’s (NIST) search for a more secure and efficient encryption method to replace the aging DES. After an extensive selection process, the Rijndael algorithm emerged as the winner, and it was officially adopted as the AES in 2001. Today, AES is used by governments, businesses, and individuals worldwide to protect sensitive information and secure digital communications. Its versatility and strength have made it the go-to choice for a wide range of applications, from encrypting files and database records to securing data transmitted over networks.
Understanding AES
AES as a symmetric key algorithm
Symmetric key encryption is a type of encryption where the same key is used to both encrypt and decrypt data. This means that when you want to send encrypted data to someone else, you’ll need to securely share the key with the recipient beforehand. Once they have the key, they can then decrypt the data and access the original information. Asymmetric key encryption, on the other hand, uses a pair of keys for encryption and decryption: a public key and a private key. The public key can be freely shared and is used to encrypt data, while the private key is kept secret and is used to decrypt data. This eliminates the need for securely exchanging keys, which can be a challenge in itself. However, asymmetric encryption tends to be slower and less efficient compared to symmetric encryption, which is why symmetric key algorithms like AES are often preferred for bulk data encryption.
The development of AES
There are several key strengths and features that set AES apart from its predecessor, DES, and other encryption algorithms. One of the main advantages of AES is its flexibility in terms of key length. AES supports key lengths of 128, 192, and 256 bits, providing varying levels of security depending on the needs of the user. With a larger key size comes increased security, making it more difficult for attackers to crack the encryption through brute-force methods. Additionally, AES is designed to be efficient and fast, making it suitable for use in a wide range of applications and devices, from high-performance servers to resource-constrained IoT devices.
How AES Works
Explanation of AES encryption process
Key expansion
The AES encryption process begins with key expansion. In this step, the original key (either 128, 192, or 256 bits) is used to generate an extended key schedule, which consists of multiple round keys that will be used throughout the encryption process. This key expansion phase is crucial for ensuring that the encryption remains secure and resistant to attacks.
Initial round
After the key expansion, the initial round of the AES encryption process takes place. This round consists of a single operation called AddRoundKey, where the input data (plaintext) is combined with the first round key from the key schedule using bitwise exclusive-or (XOR) operations. This initial round helps to add some initial confusion to the plaintext before the main rounds begin.
Main rounds
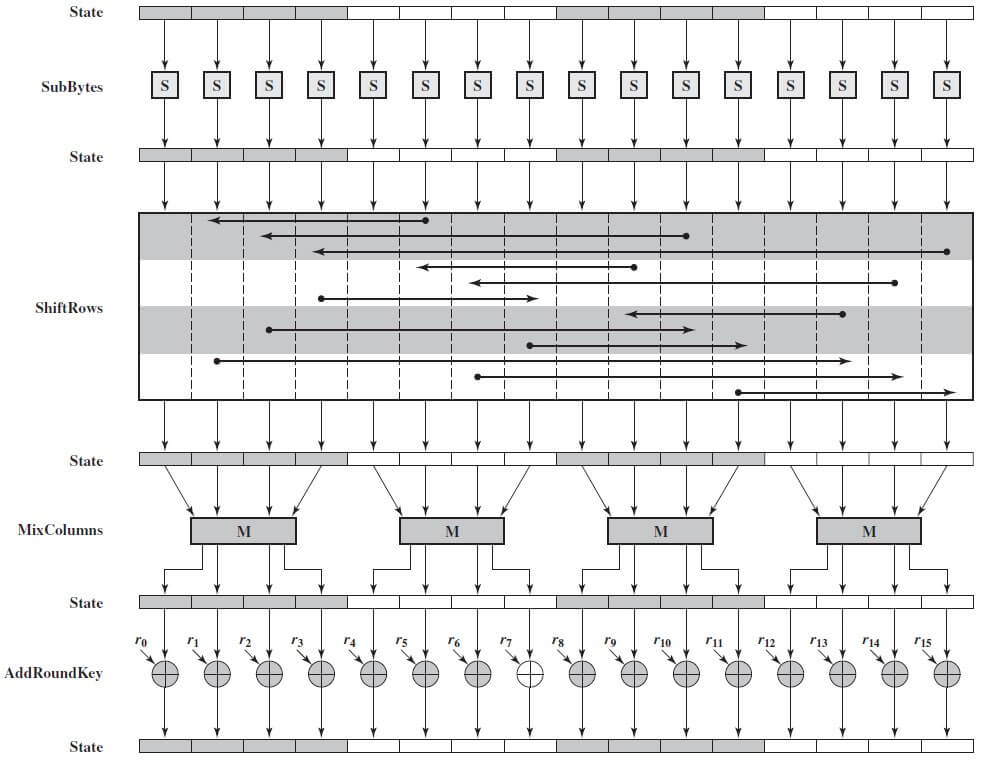
The main rounds are where the magic really happens. Depending on the key size, AES goes through a series of 10, 12, or 14 main rounds, with each round consisting of four distinct operations: SubBytes, ShiftRows, MixColumns, and AddRoundKey.
- SubBytes: A non-linear substitution step where each byte in the data matrix is replaced with its corresponding value from a predefined substitution table (S-box).
- ShiftRows: A transposition step where the rows of the data matrix are shifted by a certain offset, effectively mixing the data horizontally.
- MixColumns: Another transposition step that mixes the data vertically, providing further diffusion across columns.
- AddRoundKey: The round key from the key schedule is XORed with the data matrix, adding another layer of confusion.
These operations are performed sequentially, with the output from one round being fed into the next round.
Final round
After the main rounds have been completed, a final round is performed. This round consists of only three operations: SubBytes, ShiftRows, and AddRoundKey. Notice that the MixColumns operation is omitted in the final round to facilitate the decryption process. Once the final round is complete, the encrypted data (ciphertext) is produced.
Description of AES decryption process
Inverse key expansion
The key schedule generated during the encryption process is used in reverse order for decryption. The round keys are applied in the opposite sequence to ensure proper decryption.
Inverse initial round
The decryption process starts with an inverse initial round, which consists of a single operation: Inverse AddRoundKey. The ciphertext is XORed with the last round key from the key schedule.
Inverse main rounds
The inverse main rounds follow the inverse initial round, with each round consisting of four operations: Inverse ShiftRows, Inverse SubBytes, Inverse AddRoundKey, and Inverse MixColumns. These operations are the reverse of their corresponding encryption operations and are performed sequentially.
Inverse final round
The decryption process ends with an inverse final round that includes only three operations: Inverse ShiftRows, Inverse SubBytes, and Inverse AddRoundKey. The output of the inverse final round is the original plaintext data.
AES in Application Security
Integration of AES in secure communication protocols
Secure Socket Layer (SSL) and Transport Layer Security (TLS)
AES plays a pivotal role in secure communication protocols like Secure Socket Layer (SSL) and its successor, Transport Layer Security (TLS). These protocols are widely used to secure data transmitted over networks, such as when you access a website using HTTPS. By incorporating AES as one of the supported symmetric key encryption algorithms, SSL and TLS can provide strong confidentiality and integrity protection for data in transit.
Secure Shell (SSH)
Another important communication protocol that relies on AES is Secure Shell (SSH), which is used to establish secure, encrypted connections between remote systems. SSH can use a variety of encryption algorithms, with AES being one of the most popular choices due to its performance and security. By using AES, SSH ensures that data transmitted between systems remains confidential and secure from eavesdropping.
AES in database encryption
Transparent Data Encryption (TDE)
Databases are often a treasure trove of sensitive information, and AES plays a key role in keeping this data secure. One method of protecting stored data is through Transparent Data Encryption (TDE), which encrypts the entire database at rest. By employing AES, TDE ensures that even if an attacker gains access to the database files, they won’t be able to read the sensitive data without the decryption key.
Column-level encryption
In addition to TDE, AES can also be used for more fine-grained encryption within databases, such as column-level encryption. This approach involves encrypting only specific columns that contain sensitive data, like credit card numbers or Social Security numbers. By using AES for column-level encryption, organizations can protect sensitive information without encrypting the entire database, thus reducing the performance overhead.
AES in mobile applications
Secure storage of sensitive data
Mobile applications often handle sensitive data, such as user credentials, personal information, or financial transactions. AES is frequently used to encrypt this data when stored on the device, ensuring that even if an attacker gains access to the device’s storage, they won’t be able to read the sensitive information without the decryption key.
Encrypting communication between mobile apps and servers
When mobile applications communicate with backend servers to transmit or receive data, it’s important to ensure the confidentiality and integrity of this data in transit. AES is commonly used in conjunction with secure communication protocols like TLS to encrypt data exchanged between mobile apps and servers, protecting it from eavesdropping and tampering.
Conclusion
Throughout this blog post, we’ve seen how AES, as a widely-used symmetric key encryption algorithm, plays a crucial role in various aspects of application security. From secure communication protocols like SSL, TLS, and SSH to database encryption and password storage, AES provides a strong foundation for securing sensitive data in transit and at rest. Its flexibility in key sizes and robust resistance to attacks make it a go-to choice for many security-conscious developers and organizations. As the cybersecurity landscape continues to evolve and new threats emerge, it’s essential to stay informed about encryption standards and practices. In conclusion, I encourage you to prioritize security in your application development process. Ensuring that your applications use secure encryption methods like AES, follow best practices in implementation, and stay up-to-date with security updates can significantly reduce the risk of data breaches and other security incidents.
About the Author:
Application Security Engineer and Red-Teamer. Over 15 years of experience in Application Security, Software Engineering and Offensive Security. OSCE3 & OSCP Certified. CTF nerd.