· Alex · security · 12 min read
How Many Keys Are Used in Symmetric Cryptography?
Applications, types of ciphers, pros and cons, key management, storage, integration with other cryptographic primitives and vulnerabilities
How Many Keys Are Used in Symmetric Cryptography?
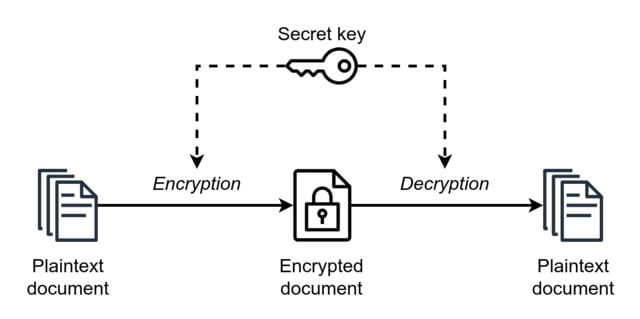
Symmetric cryptography uses a single key for both encryption and decryption, while asymmetric cryptography employs two distinct keys, one for each process. These two types of cryptography each have their unique set of advantages and challenges, which we’ll delve into later on.
Understanding Symmetric Cryptography
Definition and key principles
Symmetric cryptography, is an encryption technique where the same key is used for both encrypting and decrypting the data. It’s like having a single, shared secret that both the sender and the receiver know, and they use this secret to lock and unlock the information. The key principles of symmetric cryptography include confidentiality, integrity, and authentication, ensuring that only authorized parties can access and modify the encrypted data.
How symmetric encryption works
- Key generation: First, a secret key is generated. This key can be a random sequence of bits, a password, or even a passphrase. The strength of the encryption relies heavily on the key’s randomness and complexity.
- Encryption: The sender takes the plain text (the original, readable data) and uses the secret key to perform a series of mathematical operations, transforming the plain text into ciphertext (the encrypted, unreadable data).
- Transmission: The ciphertext is then transmitted over a communication channel, such as the internet, to the intended recipient.
- Decryption: Upon receiving the ciphertext, the recipient uses the same secret key to reverse the encryption process and convert the ciphertext back into plain text.
Real-world examples of symmetric cryptography
Symmetric cryptography is widely used across various industries, thanks to its speed and efficiency. Here are some real-world examples where symmetric encryption shines:
- Secure file storage: Cloud storage services, like Dropbox and Google Drive, use symmetric encryption to protect your files while they’re stored on their servers.
- Secure communications: Messaging apps, such as WhatsApp and Signal, employ symmetric encryption to ensure that your messages remain private and secure between you and the recipient.
- Financial transactions: When you use your credit card online or at a physical store, symmetric encryption is often utilized to safeguard your sensitive financial information during the transaction process.
- Wireless security: Wi-Fi networks, particularly those that use WPA2 and WPA3 security protocols, rely on symmetric encryption to keep your data safe as it travels through the airwaves.
Types of Symmetric Encryption Algorithms
Stream ciphers
- Overview and examples
Stream ciphers are a type of symmetric encryption algorithm that encrypts data one bit or byte at a time. They work by generating a continuous stream of pseudorandom key material, known as a keystream, which is then combined with the plaintext using bitwise operations (usually XOR) to produce the ciphertext. Some popular examples of stream ciphers include:
- RC4: A widely-used stream cipher that was once the go-to choice for securing web traffic, wireless networks, and many other applications. However, it has since been deprecated due to various security vulnerabilities.
- Salsa20/ChaCha20: Modern and efficient stream ciphers designed by Daniel J. Bernstein, which are considered secure and have been adopted by several cryptographic protocols, including TLS and the secure messaging app Signal.
- Advantages and disadvantages
Advantages:
- Speed: Stream ciphers are generally faster than block ciphers, especially when it comes to encrypting large amounts of data, making them suitable for real-time applications.
- Low resource usage: They require less memory and computational power, which is beneficial for constrained environments like embedded systems or IoT devices.
Disadvantages:
- Sensitivity to synchronization issues: Stream ciphers can be vulnerable to attacks if the synchronization between the sender and receiver is lost or if the same key is used more than once.
- Lack of built-in integrity protection: Unlike some block ciphers, stream ciphers don’t inherently provide data integrity, which means additional mechanisms are often needed to ensure the data hasn’t been tampered with during transmission.
Block ciphers
- Overview and examples
Block ciphers, on the other hand, operate on fixed-size blocks of plaintext and ciphertext, usually ranging from 64 to 256 bits. They work by iteratively applying a series of transformations, called rounds, to the plaintext using a secret key. These rounds typically include substitution, permutation, and mixing operations. Some well-known examples of block ciphers include:
- DES (Data Encryption Standard): An older block cipher that uses a 56-bit key and a 64-bit block size. It has been largely replaced by more secure alternatives due to its vulnerability to brute-force attacks.
- AES (Advanced Encryption Standard): A widely-used and highly-regarded block cipher that supports key sizes of 128, 192, and 256 bits, with a fixed block size of 128 bits. AES is the go-to choice for many security applications and is considered the gold standard in symmetric encryption.
- Advantages and disadvantages
Advantages:
- Robustness: Block ciphers generally provide strong resistance against various types of cryptographic attacks when properly implemented.
- Versatility: They can be used in different modes of operation, such as CBC, CTR, or GCM, which allows them to function like stream ciphers or provide built-in integrity protection.
Disadvantages:
- Slower performance: Compared to stream ciphers, block ciphers can be slower, especially when encrypting small amounts of data or in real-time applications.
- Padding requirements: Since block ciphers operate on fixed-size blocks, they often require padding to fill the last block, which can add complexity to the encryption and decryption process.
Key Management in Symmetric Cryptography
Importance of key management
Key management is the process of creating, distributing, storing, and protecting cryptographic keys in a secure manner. It’s the foundation of any effective symmetric encryption system because, without proper key management, even the strongest encryption algorithm can be rendered useless. Effective key management helps prevent unauthorized access, ensures data confidentiality, and maintains the overall security of the encrypted information.
Key generation
The first step in key management is key generation. This process involves creating a random, unique, and strong secret key to be used for encryption and decryption. In symmetric cryptography, the strength of the encryption largely depends on the randomness and complexity of the key. Keys can be generated using various methods, such as:
- Pseudorandom number generators (PRNGs): These algorithms produce sequences of numbers that appear random but are derived from an initial value, called a seed. Cryptographically secure PRNGs (CSPRNGs) are preferred for key generation, as they exhibit higher levels of unpredictability and resistance to prediction.
- Hardware random number generators (HRNGs): These devices generate true random numbers by measuring physical processes, such as electronic noise or radioactive decay, providing a higher degree of randomness compared to PRNGs.
Key distribution
Once a key is generated, it must be securely distributed to all parties involved in the encrypted communication. This is often considered the Achilles’ heel of symmetric cryptography, as the key distribution process can be vulnerable to attacks, such as eavesdropping or man-in-the-middle (MITM) intrusions. To address this issue, various key distribution techniques have been developed, including:
- Pre-shared keys: The secret key is agreed upon or exchanged in person before communication begins, ensuring no third party can intercept it.
- Key exchange protocols: Algorithms like the Diffie-Hellman key exchange allow parties to securely agree on a shared secret key, even over an insecure channel.
- Using asymmetric encryption: Asymmetric encryption, such as RSA or Elliptic Curve Cryptography (ECC), can be employed to securely transmit the symmetric key between parties.
Key storage and protection
Finally, after generating and distributing the secret key, it must be securely stored and protected from unauthorized access. Key storage and protection measures can include:
- Encryption: Encrypting the secret key with another key or password provides an additional layer of security.
- Hardware security modules (HSMs): These specialized devices are designed to securely generate, store, and manage cryptographic keys, protecting them from physical and logical attacks.
- Key management systems (KMS): A KMS can help automate and centralize the management of cryptographic keys, providing secure storage, access control, and auditing capabilities.
Key Sizes and Security
Relationship between key size and security
In symmetric cryptography, the key size is the number of bits that make up the secret key. The key size directly impacts the security of the encryption, as a longer key means there are more possible combinations to try when attempting to crack the code. Simply put, the larger the key size, the more secure the encryption – up to a certain point, of course, as there are diminishing returns and practical considerations to take into account.
Common key sizes for symmetric encryption algorithms
Symmetric encryption algorithms come with various key size options, depending on their design and the desired security level. Some common key sizes for popular symmetric encryption algorithms include:
- DES (Data Encryption Standard): Uses a 56-bit key, which is now considered insecure due to advancements in computing power.
- 3DES (Triple DES): Applies the DES algorithm three times with either two (112 bits) or three (168 bits) independent keys. Though more secure than DES, 3DES is also slower and being phased out in favor of more modern algorithms.
- AES (Advanced Encryption Standard): Offers key sizes of 128, 192, and 256 bits. AES is widely used and considered highly secure, with the larger key sizes providing even greater resistance to attacks.
Factors influencing the choice of key size
When choosing a key size for your symmetric encryption implementation, several factors should be considered:
- Security requirements: Consider the sensitivity of the data being encrypted and the potential impact of a security breach. Highly sensitive information may warrant larger key sizes for added protection.
- Performance: Larger key sizes can result in slower encryption and decryption times. Depending on the application, it might be necessary to strike a balance between security and performance.
- Compliance and standards: Some industries and applications have specific requirements or guidelines when it comes to key sizes, such as payment processing (PCI DSS) or government use (NIST recommendations).
- Future-proofing: With the constant increase in computing power, it’s important to consider how long the encrypted data needs to remain secure and whether the chosen key size will provide adequate protection in the future.
Brute-force attacks and computational security
A brute-force attack is a type of cryptanalysis where an attacker systematically tries every possible key combination until the correct key is found. The security of symmetric encryption against brute-force attacks depends on the key size and the computational power available to the attacker. For example, a 56-bit key (as used in DES) has 2^56 possible combinations, which was once considered secure but can now be cracked within minutes using modern hardware. On the other hand, a 128-bit AES key has 2^128 possible combinations, which, with current technology, would take billions of years to crack via brute force. The concept of computational security implies that the encryption is considered secure as long as the time and resources needed to break it through brute force are impractical or unattainable.
Challenges and Limitations of Symmetric Cryptography
Key distribution problem
As we’ve touched on earlier, one of the main challenges in symmetric cryptography is securely distributing the secret key to all parties involved in the encrypted communication. If the secret key is intercepted or leaked during the distribution process, the entire encryption system is compromised.
Vulnerability to certain attacks
While symmetric encryption algorithms are typically resistant to various types of attacks when implemented correctly, they are not immune to all threats. Some of the potential vulnerabilities in symmetric cryptography include:
- Chosen plaintext attacks (CPA): In this scenario, an attacker can obtain the ciphertext corresponding to specific plaintexts of their choice. If the encryption algorithm is vulnerable to CPA, the attacker may be able to infer some information about the secret key.
- Chosen ciphertext attacks (CCA): These attacks involve the attacker choosing a ciphertext and obtaining the decryption of that ciphertext under the target secret key. If successful, the attacker can gain information about the plaintext or the secret key itself.
- Replay attacks: In a replay attack, an attacker intercepts and retransmits a previously captured message, tricking the recipient into accepting it as a new, legitimate message. Symmetric encryption alone cannot prevent replay attacks, requiring additional mechanisms like timestamps or sequence numbers to ensure message integrity.
Symmetric Cryptography in Practice
Integration with other cryptographic techniques
In practice, symmetric encryption is often used in conjunction with other cryptographic techniques to provide a more comprehensive security solution. Some common integrations include:
- Asymmetric encryption: As we mentioned earlier, asymmetric encryption can be employed to securely exchange symmetric keys between parties, combining the efficiency of symmetric encryption with the key distribution advantages of asymmetric cryptography.
- Digital signatures: To ensure data integrity and non-repudiation, digital signatures can be used alongside symmetric encryption. For example, a sender might encrypt a message using symmetric encryption and then sign it with their private key, allowing the recipient to verify the message’s authenticity.
- Hash functions: Hash functions can be used to generate unique fingerprints of data, which can be encrypted using symmetric encryption to provide data integrity checks and tamper resistance.
Best practices for implementing symmetric encryption
When implementing symmetric encryption, adhering to best practices can help ensure the security and effectiveness of your solution:
- Choose a strong encryption algorithm: Opt for a widely-accepted and proven symmetric encryption algorithm, such as AES, which is considered secure and efficient for most applications.
- Use appropriate key sizes: Balance security and performance by selecting a suitable key size based on your specific requirements and the sensitivity of the data being protected.
- Implement secure key management: Generate, distribute, store, and protect keys securely, employing techniques like hardware security modules (HSMs) or key management systems (KMS) when necessary.
- Regularly update and rotate keys: Replace keys periodically and whenever a potential compromise is suspected, reducing the risk of unauthorized access.
- Combine with other cryptographic techniques: Integrate symmetric encryption with other security mechanisms, like asymmetric encryption, digital signatures, or hash functions, to create a more robust and comprehensive solution.
Conclusion
Symmetric cryptography is an essential component of secure communication and data protection. It involves the use of a single secret key to both encrypt and decrypt information, offering a fast and efficient means of safeguarding sensitive data. Symmetric encryption is a vital piece of the security puzzle, but it’s important to recognize that it’s just one part of a comprehensive security strategy. In practice, symmetric cryptography is often integrated with other cryptographic techniques, such as asymmetric encryption, digital signatures, and hash functions, to provide a more robust and secure solution. Understanding the strengths and limitations of symmetric encryption, as well as how it can be combined with other security mechanisms, enables us to create effective security strategies that protect our digital world.
About the Author:
Application Security Engineer and Red-Teamer. Over 15 years of experience in Application Security, Software Engineering and Offensive Security. OSCE3 & OSCP Certified. CTF nerd.



