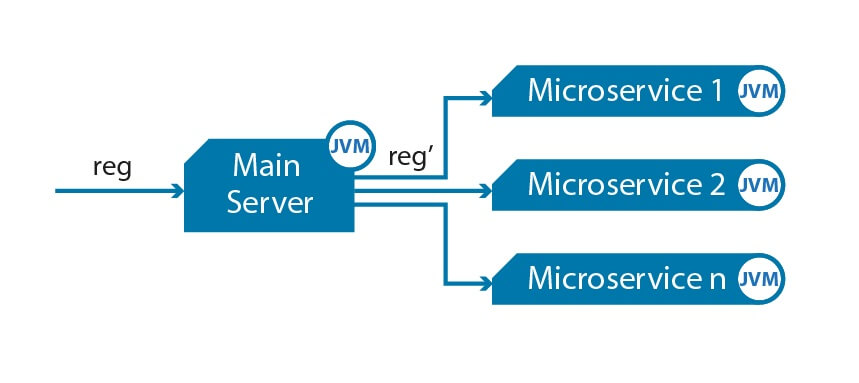
· Alex · security · 7 min read
OWASP Guide
A quick run down of the most important projects OWASP has to offer in regards to securing applications
OWASP Guide
OWASP, or the Open Web Application Security Project, is a global non-profit organization that’s dedicated to improving web application security. They provide a wealth of resources and tools to help developers and organizations better understand and address the risks associated with web applications.
Key Components
- The OWASP Top Ten Project: This is a list of the ten most critical web application security risks, updated every few years. It’s a great starting point for understanding the most common threats and vulnerabilities in web applications. By addressing these top risks, you’ll be well on your way to building a more secure web app.
- The OWASP Testing Guide: This one’s all about web application security testing. It provides a comprehensive methodology for testing your application for vulnerabilities, as well as a detailed list of test cases for various security issues. If you’re serious about making your web app as secure as possible, you’ll definitely want to get familiar with this guide.
- The OWASP Code Review Guide: Code review is an essential step in ensuring the security of your web application. The Code Review Guide offers practical advice and best practices for conducting secure code reviews. It highlights key security areas to focus on during the review process, so you can be confident that your code is rock-solid.
- The OWASP Application Security Verification Standard (ASVS): Last but not least, the ASVS is a set of guidelines for verifying the security of your web application during development and testing. It complements the OWASP Code Review Guide and helps you ensure that your application meets a certain level of security. By incorporating the ASVS into your development process, you can systematically reduce the risk of security vulnerabilities in your web app.
The OWASP Top Ten Project
Overview of the Top Ten Project
Alright, let’s kick things off with the famous OWASP Top Ten Project. The history of this project dates back to 2003, when OWASP compiled a list of the most critical web application security risks. The goal was to raise awareness about the most common vulnerabilities and encourage developers to take security more seriously. The list has evolved over the years, with new risks being added and old ones being updated, but the core mission remains the same: to make the web a safer place for everyone. So why is the Top Ten Project such a big deal in the industry? Well, it’s become a go-to resource for developers and organizations worldwide. It helps them understand the most pressing security risks and serves as a baseline for web application security. By addressing the Top Ten risks, you’re effectively tackling a large chunk of the security issues that commonly plague web applications. For a deeper dive into this subject see my post on The OWASP Top Ten Project.
The OWASP Testing Guide
Introduction to Web Application Security Testing
So, we’ve talked about the risks, but how do we actually test our web applications to ensure they’re secure? That’s where the OWASP Testing Guide comes in! Thorough security testing is essential because it helps you identify and address vulnerabilities before they can be exploited by attackers. There are different types of testing, including manual testing (where a human tester actively explores the application for security flaws) and automated testing (where tools scan the application for known vulnerabilities).
Key Components of the OWASP Testing Guide
The OWASP Testing Guide is a comprehensive resource that covers all aspects of web application security testing. Here are some of the key components of the guide:
- Testing Methodology and Phases: The guide provides a structured methodology for testing, consisting of four phases—planning, discovery, vulnerability assessment, and reporting. This ensures a systematic approach to testing that leaves no stone unturned.
- Major Categories of Tests: The guide organizes test cases into various categories, such as authentication, session management, input validation, and access control. This helps you focus on specific areas of your application and prioritize testing efforts.
- Test Cases and Examples: The guide includes detailed test cases for each category, along with examples and guidance on how to perform the tests. This makes it easy for testers to understand and implement the tests in their own applications.
Implementing the OWASP Testing Guide
Now that you know what the OWASP Testing Guide is all about, let’s talk about how to actually implement it in your development process:
- Integrating Testing into the Development Life Cycle: Security testing should be an integral part of your development life cycle, not an afterthought. By incorporating testing early and often, you can catch vulnerabilities before they make it into production, saving you time and resources in the long run.
- Tools and Resources for Effective Testing: There are a variety of tools and resources available to help you conduct effective web application security testing. Some popular choices include OWASP Zed Attack Proxy (ZAP) for automated scanning, Burp Suite for manual testing and vulnerability scanning, and OWASP WebScarab for analyzing web application traffic.
By implementing the OWASP Testing Guide in your development process, you’ll be well-equipped to identify and address security vulnerabilities in your web applications, keeping your users and data safe from potential cyber threats.
The OWASP Code Review Guide and ASVS
Code Review for Security
Let’s talk about another critical aspect of web application security: code review. Secure code review is essential because it helps identify and fix security vulnerabilities at the code level. By thoroughly examining your code, you can catch issues that might not be apparent during testing. However, code review can be challenging, as it requires a deep understanding of the application’s functionality, as well as knowledge of potential security pitfalls and best practices.
The OWASP Code Review Guide
This resource aims to help you conduct secure code reviews effectively by providing the following:
- Code Review Objectives and Methodology: The guide outlines the primary objectives of secure code review, such as identifying security vulnerabilities and ensuring compliance with best practices. It also provides a methodology for conducting code reviews, including planning, scoping, and executing the review process.
- Key Security Areas to Focus on During Code Review: The guide highlights specific security areas that should be the focus of your code review efforts, such as input validation, output encoding, and error handling. By concentrating on these areas, you can maximize the effectiveness of your code review and uncover potential vulnerabilities.
The OWASP Application Security Verification Standard (ASVS)
The OWASP Application Security Verification Standard (ASVS) is another valuable resource that complements the Code Review Guide. Here’s what you need to know about the ASVS:
- Purpose and Goals of ASVS: The main goal of the ASVS is to provide a set of guidelines for verifying the security of web applications during development and testing. It serves as a benchmark for security best practices and helps you ensure that your application meets a certain level of security.
- How ASVS Complements the OWASP Code Review Guide: While the Code Review Guide focuses on examining the source code, the ASVS provides a broader perspective on application security. By using both resources together, you can achieve a more comprehensive understanding of your application’s security posture.
- Integrating ASVS into Your Organization’s Development Process: To get the most out of the ASVS, you should incorporate it into your development process from the start. This includes defining security requirements based on the ASVS, conducting code reviews in line with the OWASP Code Review Guide, and verifying your application’s security using the ASVS as a reference.
Read more in my post on The OWASP Application Security Verification Standard (ASVS.
Conclusion
By implementing these OWASP Guides in your development process, you’ll be taking a proactive approach to securing your web applications. This will not only help protect your users and their data but also reduce the likelihood of costly security breaches and incidents.
About the Author:
Application Security Engineer and Red-Teamer. Over 15 years of experience in Application Security, Software Engineering and Offensive Security. OSCE3 & OSCP Certified. CTF nerd.