· Alex · security · 6 min read
Email Spoofing Prevention: Secure Your Communications and Protect Your Business
SPF, DKIM, DMARC and more
Email Spoofing Prevention
Email spoofing is like the digital equivalent of impersonating someone. Essentially, it’s when a bad actor sends an email that appears to come from a legitimate source, like your bank, when it’s actually from a malicious source. They do this by manipulating email headers, sender addresses, and other technical elements to make it look like the real deal.
Prevalence of email spoofing attacks
Unfortunately, email spoofing attacks are more common than you might think. According to a report by the FBI, Business Email Compromise (BEC) scams, which often involve email spoofing, accounted for over $1.8 billion in losses in 2020 alone. That’s a staggering number, and it shows just how critical it is to stay vigilant and protect yourself from these attacks.
Understanding Email Spoofing
How email spoofing works
Forging email headers
Email headers are the hidden metadata that accompanies every email you send or receive. They contain information like the sender, recipient, and subject, among other details. Attackers can manipulate these headers to make it look like the email is coming from someone else, effectively disguising their true identity.
Email Spoofing Prevention Strategies
Sender Policy Framework (SPF)
How SPF works
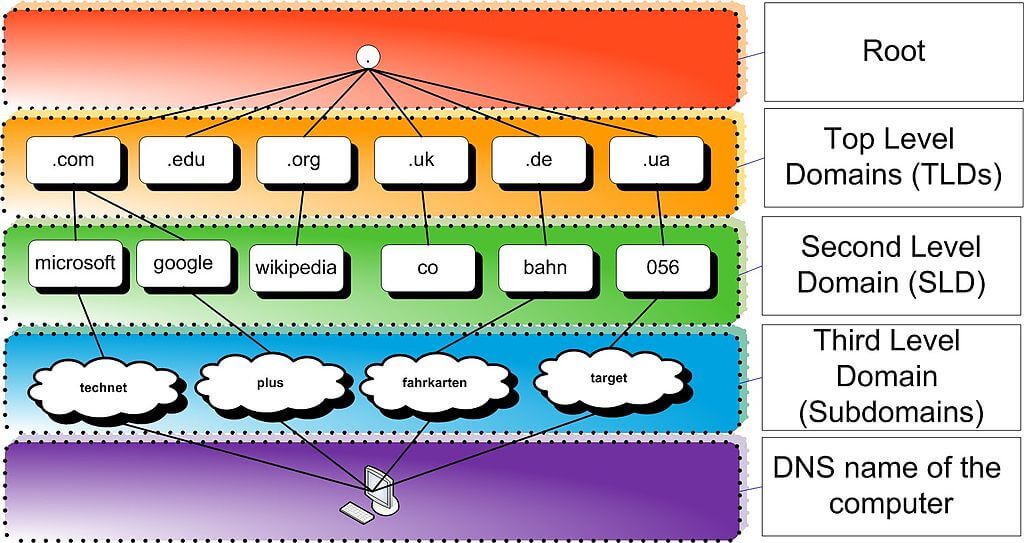
SPF is an email validation system designed to prevent email spoofing by verifying that an email is sent from an authorized server. It does this by checking the sender’s IP address against a list of approved IP addresses specified in the domain’s DNS records.
Implementing SPF records
To implement SPF, you’ll need to create a TXT record in your domain’s DNS settings. This record should list all the authorized IP addresses and mail servers that are allowed to send emails on behalf of your domain. Once you’ve set up the SPF record, receiving mail servers will be able to verify the authenticity of emails coming from your domain.
Limitations of SPF
While SPF is a valuable tool in preventing email spoofing, it does have some limitations. For example, SPF does not protect against email forwarding or verify the content of the email itself. Additionally, some receiving mail servers may not fully support SPF, which could lead to false positives or negatives.
DomainKeys Identified Mail (DKIM)
How DKIM works
DKIM is an email authentication method that uses cryptographic signatures to verify the authenticity of an email. When an email is sent, the originating server adds a digital signature to the email header. The receiving server then checks this signature against a public key stored in the domain’s DNS records to confirm that the email is genuine.
Implementing DKIM
To set up DKIM, you’ll need to generate a public-private key pair and add the public key to your domain’s DNS records as a TXT record. You’ll also need to configure your mail server to sign outgoing emails with the private key. This way, receiving servers can verify the authenticity of your emails using the public key.
Domain-based Message Authentication, Reporting, and Conformance (DMARC)
How DMARC works
DMARC is an email authentication protocol that builds upon SPF and DKIM by providing a consistent policy for handling unauthenticated emails. With DMARC, domain owners can specify how receiving mail servers should treat emails that fail SPF or DKIM checks, such as quarantining or rejecting them.
Implementing DMARC
To implement DMARC, you’ll need to create a DMARC record in your domain’s DNS settings. This record specifies your desired policy and may include an email address for receiving reports on authentication failures. By configuring DMARC, you can gain better visibility into your email security and help prevent email spoofing.
Benefits of DMARC
DMARC provides several benefits, including improved email deliverability, increased visibility into authentication failures, and a stronger defense against email spoofing attacks. By combining DMARC with SPF and DKIM, you can significantly enhance your email security.
Training and Awareness
Importance of employee training
Employee training plays a critical role in preventing email spoofing attacks. By teaching your team to recognize and respond to suspicious emails, you can significantly reduce the risk of falling victim to spoofing, phishing, and other cyber threats. A well-informed workforce is one of the best defenses against email-based attacks.
Best practices for email security
Verifying email senders
Encourage employees to double-check the sender’s email address before opening or responding to emails. Train them to look for subtle differences in domain names or display names that could indicate a spoofed email.
Identifying phishing and spoofed emails
Teach your team to be cautious of emails with urgent requests, threats, or offers that seem too good to be true. Show them examples of common phishing tactics and provide guidelines on how to spot the red flags of a spoofed email.
Reporting suspicious emails
Create a clear process for employees to report suspicious emails to your IT or security team. This not only helps protect your organization but also provides valuable insights into the types of attacks targeting your company.
Utilizing simulated phishing campaigns
One effective way to test and reinforce employee training is through simulated phishing campaigns. These exercises involve sending fake phishing emails to your employees to see how they respond. By analyzing the results, you can identify areas where your team may need additional training and adjust your programs accordingly. Simulated phishing campaigns also serve as a valuable reminder to employees about the importance of email security and the ongoing threat of email spoofing attacks.
Advanced Email Security Solutions
In addition to implementing authentication protocols and raising employee awareness, there are several advanced email security solutions that can help protect your organization from email spoofing and other cyber threats. There are commercial email gateways like Proofpoint that help with email spoofing detection, containment and more.
Integrating email security with other security measures
Finally, it’s essential to integrate your email security efforts with other security measures across your organization. This can include network security, intrusion detection systems, and security information and event management (SIEM) tools. By creating a comprehensive security framework that includes email security, you can better protect your organization from a wide range of cyber threats, including email spoofing.
Conclusion
To effectively combat email spoofing, it’s crucial to implement a multi-layered approach that includes:
- Authentication protocols like SPF, DKIM, and DMARC
- Employee training and awareness programs
- Advanced email security solutions, such as email filtering, encryption, and endpoint security
- Regular security audits
Email spoofing tactics are constantly evolving, and cyber criminals are always looking for new ways to exploit vulnerabilities. By regularly updating your security measures, training your employees, and staying informed about the latest threats, you can maintain a strong defense against email spoofing and other cyber attacks.
About the Author:
Application Security Engineer and Red-Teamer. Over 15 years of experience in Application Security, Software Engineering and Offensive Security. OSCE3 & OSCP Certified. CTF nerd.