
· Alex · security
Password Spraying
Definition, tools, and defenses against password spraying attacks

Definition, tools, and defenses against password spraying attacks

The ins and outs of drive encryption using BitLocker

How to protect your mobile device from hackers

Importance of educating developers on secure coding practices, vulnerabilities and how to create a security culture

Discuss API security, top 10 security risks and how to implement in your organization
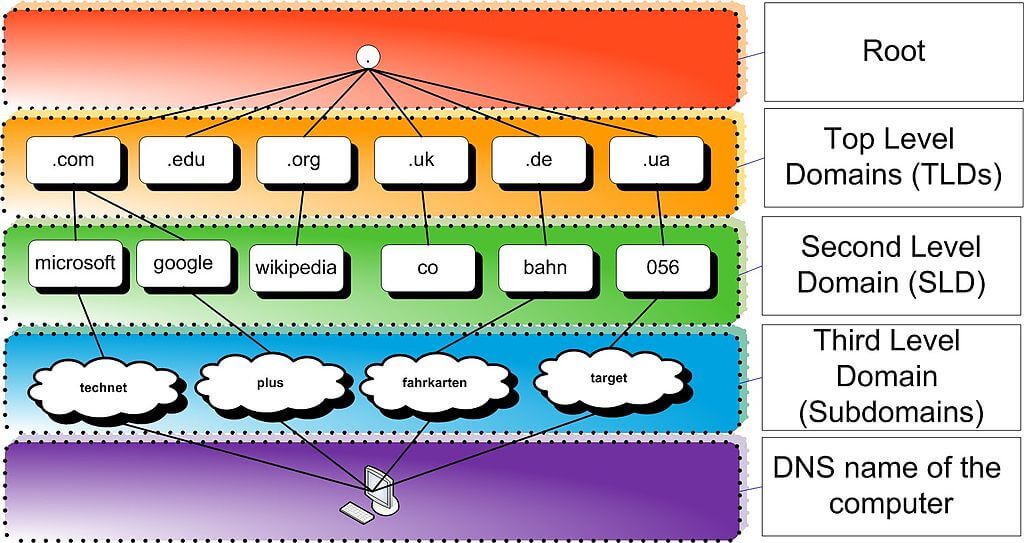
Dive into the intricacies of DNS amplification attacks, exploring their mechanics, consequences, and the strategies to detect, prevent, and respond to them.