· Alex · security · 7 min read
DNS Amplification Attacks: A Guide to Understanding and Mitigating the Threat
Dive into the intricacies of DNS amplification attacks, exploring their mechanics, consequences, and the strategies to detect, prevent, and respond to them.
DNS Amplification Attacks
DNS amplification attacks are a type of Distributed Denial of Service (DDoS) attack, leveraging the Domain Name System (DNS) to flood target systems with overwhelming amounts of traffic. Attackers exploit open recursive DNS resolvers, sending them small queries that generate massive responses. These large responses are then directed towards the victim’s IP address, causing their systems to slow down or even crash.
Understanding DNS Amplification Attacks
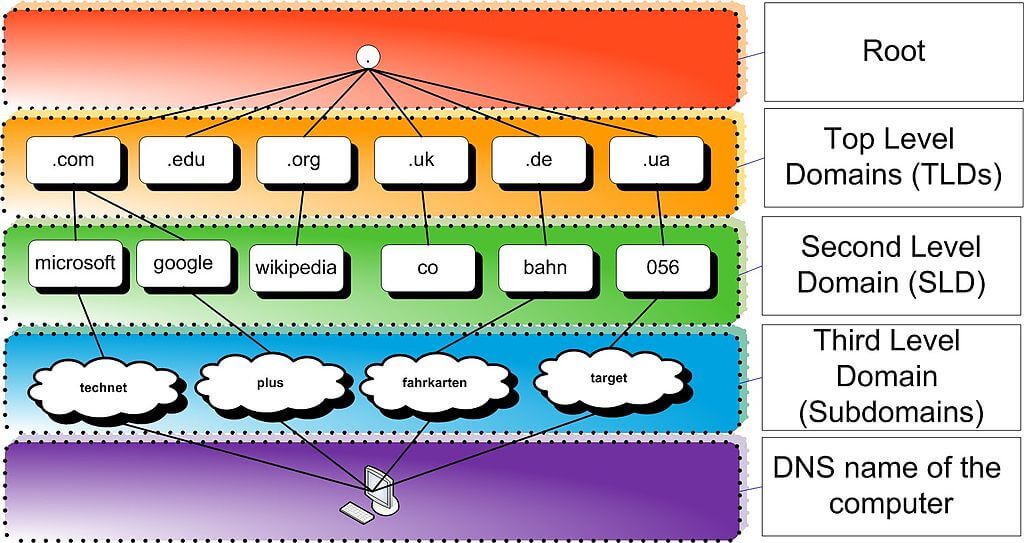
The Domain Name System (DNS)
What is DNS and its purpose?
DNS is like the internet’s phone book, translating human-friendly domain names (like example.com) into IP addresses (like 1.1.1.1) that computers can understand. Without DNS, we’d be stuck memorizing long sequences of numbers to access our favorite websites.
How DNS queries work
When you enter a URL into your browser, your computer sends a DNS query to a DNS resolver, asking for the IP address associated with the domain name. The resolver searches its cache for the requested information. If it doesn’t have the answer, it forwards the query to a series of DNS servers until it finds the correct IP address. Once the resolver receives the IP address, it sends it back to your computer, allowing you to access the website.
DNS Amplification Attack Mechanics
Exploiting DNS servers
In a DNS amplification attack, attackers exploit vulnerable DNS servers to amplify the volume of traffic sent to a target system. They use a technique called “IP address spoofing,” where they forge the source IP address in their DNS query to match the victim’s IP address. When the DNS server responds, it sends the much larger response to the victim’s IP instead of the attacker’s.
The role of open recursive DNS resolvers
DNS amplification attacks rely heavily on open recursive DNS resolvers - servers that accept DNS queries from any source, not just their own network. Attackers take advantage of these resolvers because they don’t restrict who can use them, making it easy to send a barrage of DNS queries with spoofed IP addresses.
Amplification factor
The amplification factor is what makes DNS amplification attacks so effective. By crafting a small query that generates a significantly larger response, attackers can “amplify” the amount of traffic sent to the victim’s system. In some cases, the response can be 50 to 100 times larger than the original query, creating an overwhelming flood of data that can cripple the target system.
Consequences of DNS Amplification Attacks
Impact on Targeted Systems
Denial-of-service
DNS amplification attacks can cause targeted systems to experience severe downtime, leading to a denial-of-service. As the victim’s system struggles to handle the influx of traffic, its performance is significantly degraded, or in some cases, the system becomes completely unresponsive. This disruption can have serious consequences, especially for businesses and organizations that rely on their online presence and services.
Financial and reputational damage
In addition to the direct impact on system performance, DNS amplification attacks can lead to financial losses and damage to an organization’s reputation. Companies may face revenue loss due to downtime, as well as the costs associated with mitigating the attack and recovering from it. Furthermore, customers and clients may lose trust in the affected organization, leading to long-term reputational harm.
Collateral Damage
Impact on DNS infrastructure
DNS amplification attacks don’t just affect the targeted systems; they can also cause collateral damage to the DNS infrastructure itself. When attackers exploit open recursive DNS resolvers, these servers become unwitting accomplices in the attack. As a result, their resources are consumed, and their performance may be negatively affected. This can lead to slower DNS resolution times and outages for legitimate users.
Strain on internet bandwidth
Since DNS amplification attacks generate massive amounts of traffic, they can also put a strain on internet bandwidth. This can cause network congestion and slow down internet speeds for users sharing the same network as the targeted system. In large-scale attacks, the impact can even extend to other networks and internet service providers, causing widespread disruptions.
Detecting and Preventing DNS Amplification Attacks
Detection Methods
Unusual DNS traffic patterns
To detect DNS amplification attacks, monitoring your network for unusual DNS traffic patterns is crucial. A sudden spike in DNS queries or a disproportionate amount of incoming traffic compared to outgoing traffic could indicate an ongoing attack. By establishing baseline metrics for your network, you can more easily identify anomalies and respond accordingly.
Monitoring network traffic for amplification signatures
Another effective detection method is monitoring network traffic for amplification signatures. This involves looking for specific patterns, such as a high number of DNS responses with a much larger size than the corresponding queries. By setting up alerts for such signatures, you can proactively detect potential attacks and take action to mitigate them.
Best Practices for DNS Server Operators
Disabling open recursion
DNS server operators can play a critical role in preventing DNS amplification attacks by disabling open recursion on their servers. By limiting recursion to only authorized networks and clients, you can prevent your server from being exploited by attackers to amplify their traffic.
Implementing rate limiting
Rate limiting is another effective way to protect DNS servers from being abused in amplification attacks. By limiting the number of DNS queries a server will accept from a single IP address within a specified time period, you can reduce the risk of your server being used as an amplifier in an attack.
DNS response size limiting
To further mitigate the risk of DNS amplification attacks, consider implementing DNS response size limiting. This involves configuring your DNS server to limit the size of its responses, reducing the amplification factor and making it less attractive to attackers.
Network-level Defenses
Ingress and egress filtering
Implementing ingress and egress filtering on your network can help prevent spoofed IP addresses from entering or leaving your network. This reduces the likelihood of your network being used as a source or target of DNS amplification attacks.
Blocking traffic from known malicious IP addresses
Another network-level defense is blocking traffic from known malicious IP addresses. By maintaining and regularly updating a blacklist of IP addresses associated with DNS amplification attacks, you can prevent these addresses from interacting with your network and reduce the risk of becoming a target.
Responding to DNS Amplification Attacks
Incident Response Planning
Developing a comprehensive incident response plan
Having a comprehensive incident response plan in place is essential for organizations to effectively respond to DNS amplification attacks. This plan should outline the roles and responsibilities of various team members, provide clear communication channels, and detail the procedures for detecting, containing, and mitigating an attack.
An effective incident response plan should include the following key elements:
- Clear objectives and scope
- Assignment of roles and responsibilities to team members
- Procedures for detecting and reporting incidents
- Steps for containment, eradication, and recovery
- Communication protocols for internal and external stakeholders
- Regular reviews and updates to ensure the plan remains relevant and effective
Mitigation Strategies
Traffic filtering and redirection
Once a DNS amplification attack is detected, implementing traffic filtering and redirection can help mitigate its impact. This involves analyzing incoming traffic and filtering out malicious DNS responses or redirecting them to a “sinkhole” where they can be safely absorbed without affecting your systems. Working with your internet service provider (ISP) or a DDoS mitigation service can be crucial in executing these strategies effectively.
Post-incident Recovery
Assessing the damage and learning from the attack
Once the attack has been contained and mitigated, it’s essential to assess the damage and learn from the incident. This involves analyzing the attack’s timeline, determining its root cause, and identifying any weaknesses in your systems or processes that could be exploited in the future. By conducting a thorough post-mortem, you can gain valuable insights and improve your organization’s security posture moving forward.
Implementing additional security measures
Based on the lessons learned from the attack, it’s crucial to implement additional security measures to prevent future DNS amplification attacks. This may include improving your DNS server configurations, strengthening network-level defenses, and investing in advanced detection and mitigation tools.
Conclusion
In this blog post, we’ve delved into the intricacies of DNS amplification attacks, exploring their mechanics, consequences, and the strategies to detect, prevent, and respond to them. DNS amplification attacks pose a significant threat to today’s cybersecurity landscape, causing denial-of-service, financial and reputational damage, and collateral harm to DNS infrastructure and internet bandwidth. Understanding these attacks and implementing effective mitigation strategies is essential to protect your organization and contribute to a more secure internet ecosystem.
About the Author:
Application Security Engineer and Red-Teamer. Over 15 years of experience in Application Security, Software Engineering and Offensive Security. OSCE3 & OSCP Certified. CTF nerd.