· Alex · security
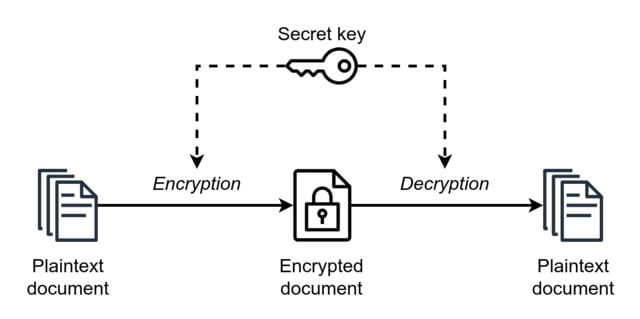
How Many Keys Are Used in Symmetric Cryptography?
Applications, types of ciphers, pros and cons, key management, storage, integration with other cryptographic primitives and vulnerabilities

Applications, types of ciphers, pros and cons, key management, storage, integration with other cryptographic primitives and vulnerabilities
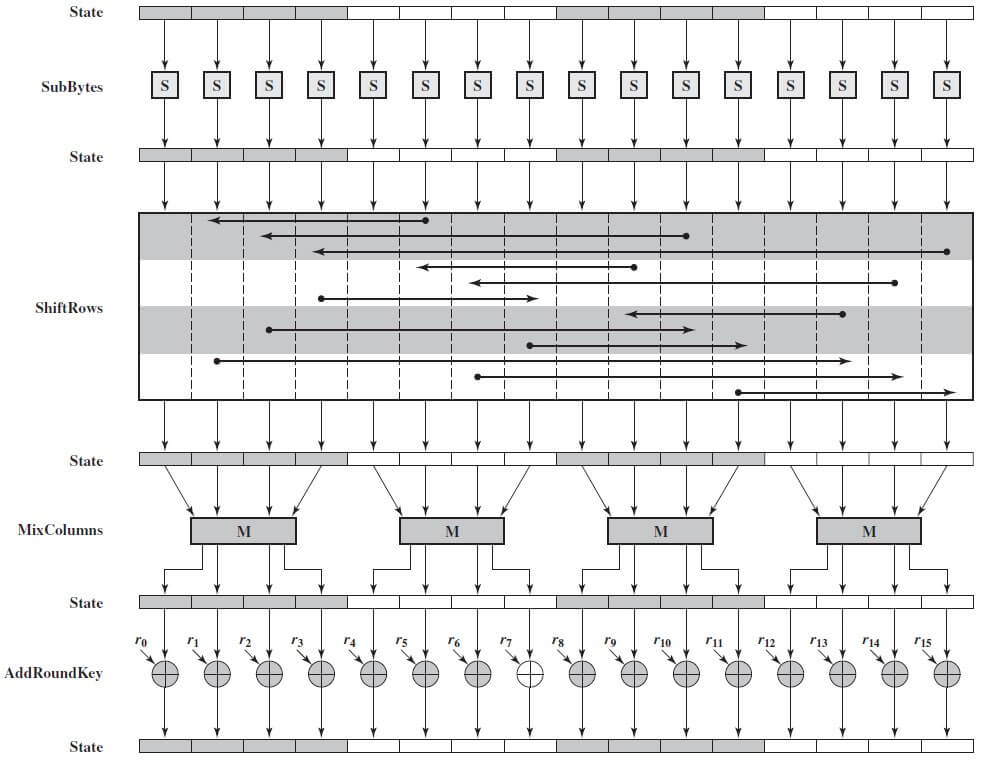
How AES works and how it applies to application security

How to use AES GCM and PBKDF2 to store an encrypted secret