
· Alex · security
What is Another Name for Asymmetric Cryptography?
How it works, real world applications, pros and cons

How it works, real world applications, pros and cons
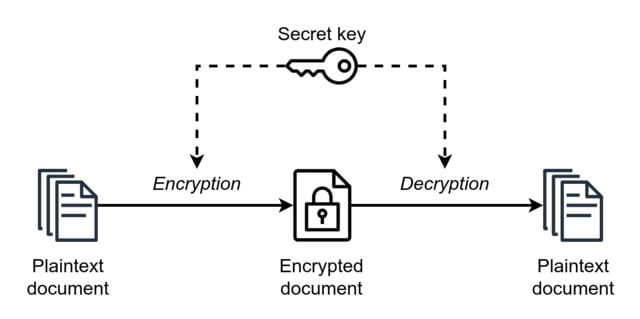
Applications, types of ciphers, pros and cons, key management, storage, integration with other cryptographic primitives and vulnerabilities