· Alex · security · 3 min read
How to Prevent Click-Jacking
A quick guide on clickjacking vulnerabilities
How to Prevent Clickjacking
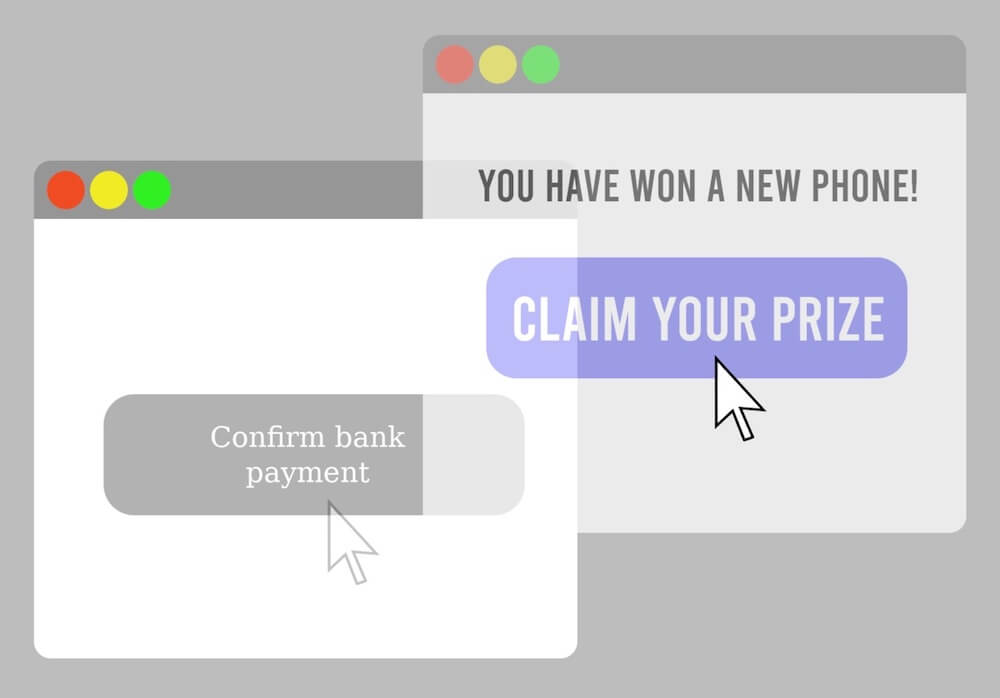
Clickjacking is a technique that bad actors use to trick users into clicking on something they didn’t intend to click on. They do this by layering invisible or misleading elements over seemingly benign web content. The user thinks they’re clicking on a harmless button or link, but in reality, they’re interacting with a hidden element that the attacker controls. Attackers can use it to steal users’ personal information, exploit their permissions on a site, or even spread malware.
Understanding Clickjacking Attacks
There are two primary techniques that attackers use to pull off a clickjacking attack:
- Invisible overlays: In this method, the attacker places an invisible or transparent layer on top of a legitimate web page. The user might think they’re interacting with the actual site, but they’re actually clicking on the hidden overlay, which is controlled by the attacker.
- Deceptive user interface elements: Another common technique is to use misleading UI elements that look like something else entirely. For example, an attacker might create a button that looks like it’ll download a file but actually triggers a different action when clicked.
There are three main objectives that attackers typically pursue when employing clickjacking techniques:
- Stealing user data: Clickjacking can be used to trick users into unknowingly submitting sensitive information, such as login credentials or personal details, to an attacker-controlled form.
- Exploiting user permissions: Some clickjacking attacks aim to exploit a user’s permissions on a website, allowing the attacker to perform actions on the user’s behalf without their knowledge or consent.
- Spreading malware: Clickjacking can also be used to trick users into downloading and installing malware, such as viruses or ransomware, on their devices.
Preventing Clickjacking Vulnerability
Proper use of browser security features:
To start, let’s explore some browser security features that can help prevent clickjacking attacks.
- Same-origin policy: This policy restricts web pages from interacting with content from different origins (i.e., different domain, protocol, or port). By enforcing the same-origin policy, we can limit the possibility of clickjacking attacks across different domains.
- Content Security Policy (CSP): CSP is a security feature that allows you to define which sources of content are allowed to be loaded by a web page. By setting a strict CSP, you can prevent unauthorized content (such as malicious iframes) from being embedded on your site.
- X-Content-Type-Options: This header prevents browsers from interpreting files as a different MIME type. By setting the X-Content-Type-Options header to “nosniff”, you can block the browser from loading potentially malicious content that might be used in a clickjacking attack.
Conclusion
In conclusion, it’s essential to take a proactive approach to application security, and addressing clickjacking vulnerabilities is just one piece of the puzzle.
About the Author:
Application Security Engineer and Red-Teamer. Over 15 years of experience in Application Security, Software Engineering and Offensive Security. OSCE3 & OSCP Certified. CTF nerd.